
September 2025 CyberAB Town Hall Recap: Enforcement Clarifications, Ecosystem Capacity, and ESP Confusion
With less than six weeks until CMMC 2.0 enforcement begins on November 10, 2025, organizations across the Defense Industrial Base are under growing pressure to prepare. The September CyberAB Town Hall offered a timely update on where things stand and what contractors, assessors, and service providers need to understand to avoid missteps in this final stretch.
This session tackled lingering confusion around external service provider (ESP) scoping, shared the latest on the rulemaking timeline, and clarified new requirements affecting both U.S. and international stakeholders. Below, we break down the key takeaways from the latest Town Hall and what they mean for your certification strategy.
The CMMC Ecosystem is growing, but will it be enough to meet demand?
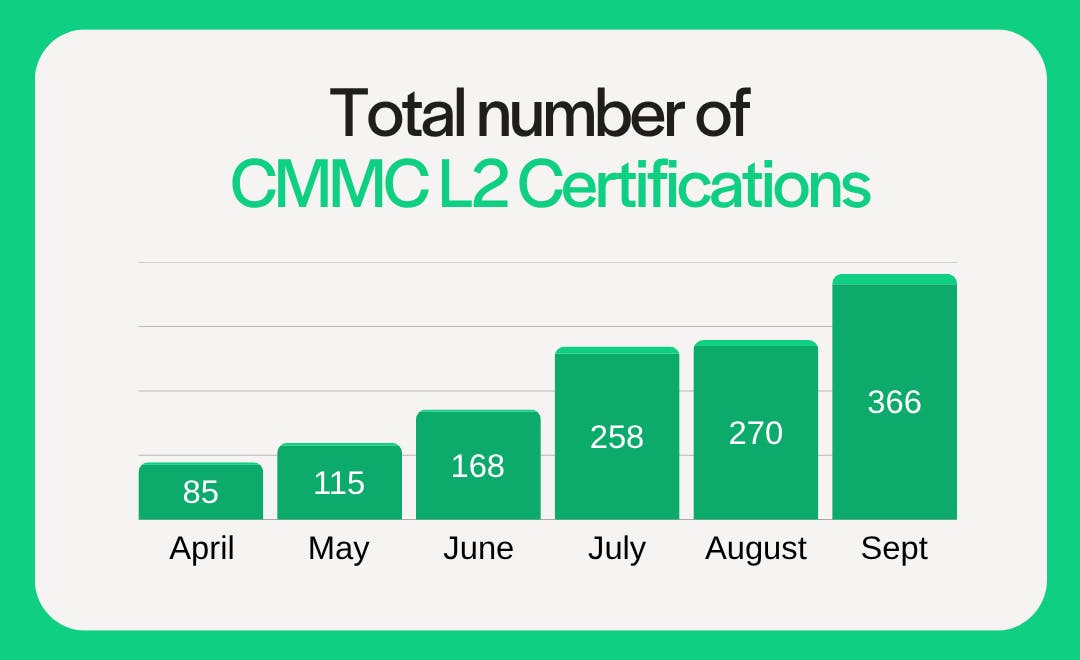
CMMC certifications are steadily increasing, though the pace remains modest given the size of the Defense Industrial Base. As of September:
- 366 organizations have received final Level 2 certification, with another 16 receiving conditional certification
- 82 C3PAOs are currently authorized or accredited
- Over 1,000 individuals hold CCP credentials
- International participation is growing, with RPs, RPOs, and CCP/CCAs now active across more than a dozen countries
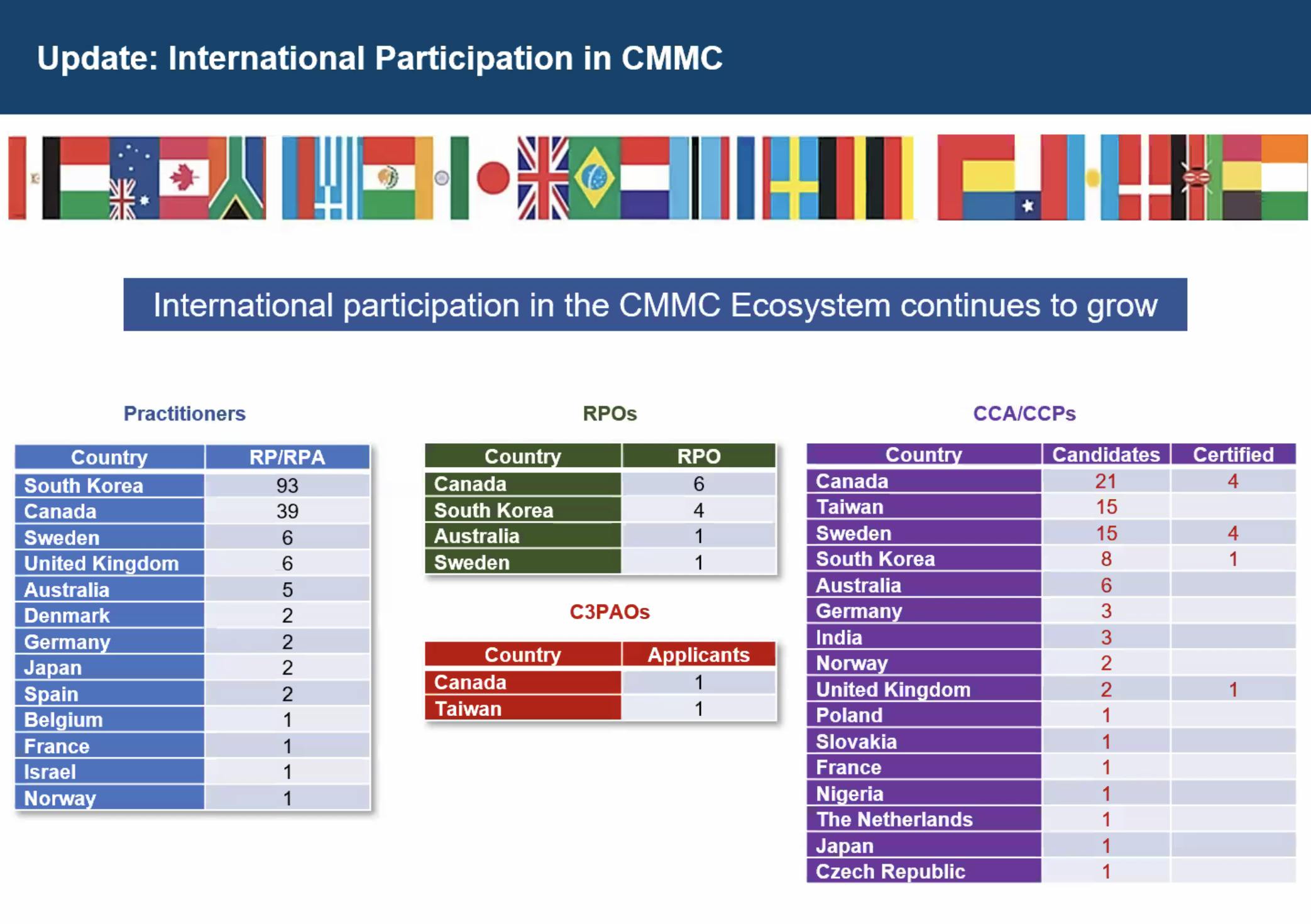
The Cyber AB clarified that international organizations applying to become C3PAOs must still undergo a full DIBCAC assessment to be authorized. Holding a Level 2 certificate is not enough.
Despite the ecosystem’s growth, many contractors are still asking: How are hundreds of thousands of defense suppliers going to get certified in time?
When do contractors actually need to be certified?
One of the most important clarifications from the September Town Hall is when exactly CMMC certification is required. While the Title 48 rule will become enforceable on November 10, 2025, contractors do not need to be certified by that date. Rather, you need to be certified before contract award if the solicitation includes a CMMC requirement.
That distinction is crucial. If a solicitation appears to require CMMC certification at the time of proposal submission, that language is likely incorrect or challengeable. As the CyberAB explained, CMMC can only be required at the point of contract award, not earlier. This aligns with existing DFARS guidance and the language in the pending Title 48 rule.
That said, contractors cannot afford to wait. Once CMMC is included in solicitations, assessors will have limited availability and OSCs will face growing competition for scheduling certification assessments. The sooner you can define your scope, implement controls, finalize your System Security Plan (SSP), and engage a C3PAO, the better positioned you’ll be when contract opportunities arise.
C3PAO Advisory Council and subcommittee activities are underway
CyberAB leadership confirmed that the C3PAO Advisory Council, which was formally launched earlier this year, has begun organizing around key focus areas. While they didn’t name all the subcommittees, they reiterated that the Council is actively contributing to:
- Assessment process interpretation and consistency
- Accreditation policy improvements
- Best practices for working with External Service Providers (ESPs)
- Clarifying roles, documentation expectations, and boundaries for assessors
Several attendees in the Q&A asked whether nominations for the Advisory Council or its subcommittees would reopen. The CyberAB was clear that no additional slots are available at this time, and that the committees are already formed and operating. So for now, those who missed the nomination deadline will need to wait for future opportunities.
Although the formal committee structure is set, the CyberAB encouraged assessors, C3PAOs, and other ecosystem participants to continue sending feedback and observations to the Council. This ensures that real-world assessment experiences inform updates to policy, the CMMC Assessment Process (CAP), and training materials.
External service providers remain a source of confusion
A large portion of this month’s Town Hall focused on scoping external service providers (ESPs), which continues to be one of the most misunderstood aspects of CMMC. According to the CyberAB, an ESP is in scope when it:
- Processes, stores, or transmits CUI on its own assets
- Handles Security Protection Data (SPD)
- Provides security for systems that process, store, or transmit

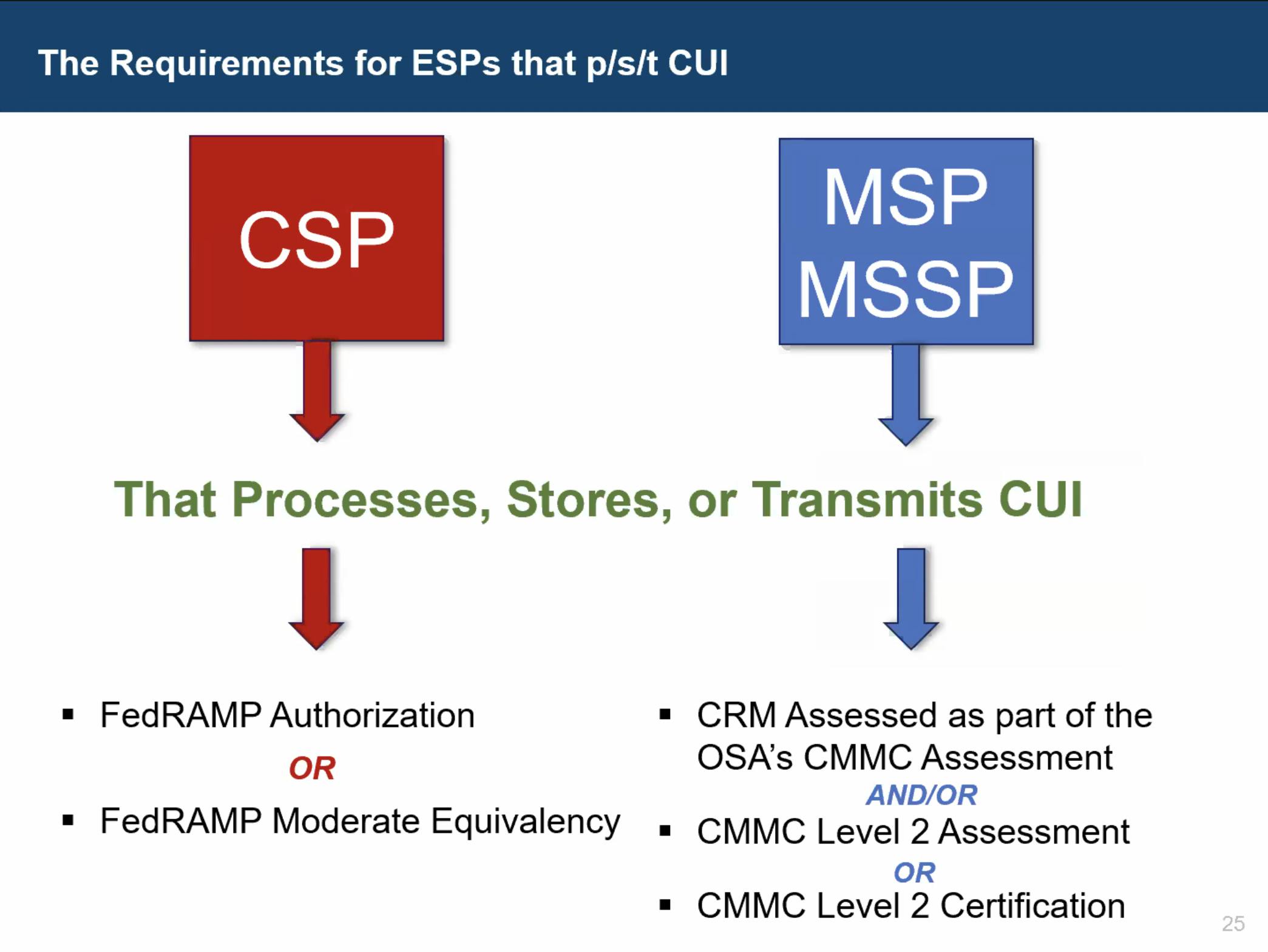
Cloud service providers (CSPs) are a specific type of ESP. For a provider to qualify as a CSP, it must meet all three NIST SP 800-145 criteria: services must be cloud-based, on-demand, and drawn from a shared pool of configurable computing resources. Many service providers do not meet all three conditions and should not be labeled CSPs, though they may still be ESPs.
The Q&A highlighted how much uncertainty around specific use cases still exist among OSCs. Several participants noted inconsistent interpretations across OSCs, C3PAOs, and CyberAB guidance. They noted that in some cases, assessors are requiring unnecessary or excessive controls for providers that may not technically be in scope. Others noted that some providers are being incorrectly categorized as CSPs, triggering FedRAMP authorization requirements they may not need to meet.
The CyberAB reiterated that documentation is key. OSCs should clearly explain in their SSP whether and how each provider fits the definition of an ESP or CSP, and what controls are in place to manage any dependencies. This documentation will be critical in avoiding assessment disputes and delays.
Prime and subcontractor responsibilities clarified
Another important Q&A clarification focused on prime and subcontractor roles. If a subcontractor handles CUI, they must obtain their own CMMC certification. The prime contractor’s certification does not extend to the sub, and the prime cannot act as an assessor on the government’s behalf.
This reinforces the idea that CMMC certification is organizational, not contractual. Each organization that handles CUI, whether directly or through security services, must demonstrate that its own systems and practices meet the required maturity level. Primes are responsible for ensuring their subcontractors are certified where appropriate, but cannot cover them under their own certification boundary.
Stay informed as CMMC enforcement takes effect
CMMC is no longer a theoretical framework, it is now a matter of federal regulation, with real timelines, penalties, and operational consequences. The November 10 rulemaking milestone is just the beginning. Contractors must be certified before award, document their ESPs properly, and ensure subcontractor compliance to stay eligible for future work.
We’ll continue to track the latest developments and CyberAB guidance. For ongoing coverage, visit the CMMC.com Newsroom or explore past Town Hall recaps: